Welcome to WordPress. This is your first post. Edit or delete it, then start writing!
Author: sgntech@yahoo.com
-
Top 8 Types of Cyber Attacks
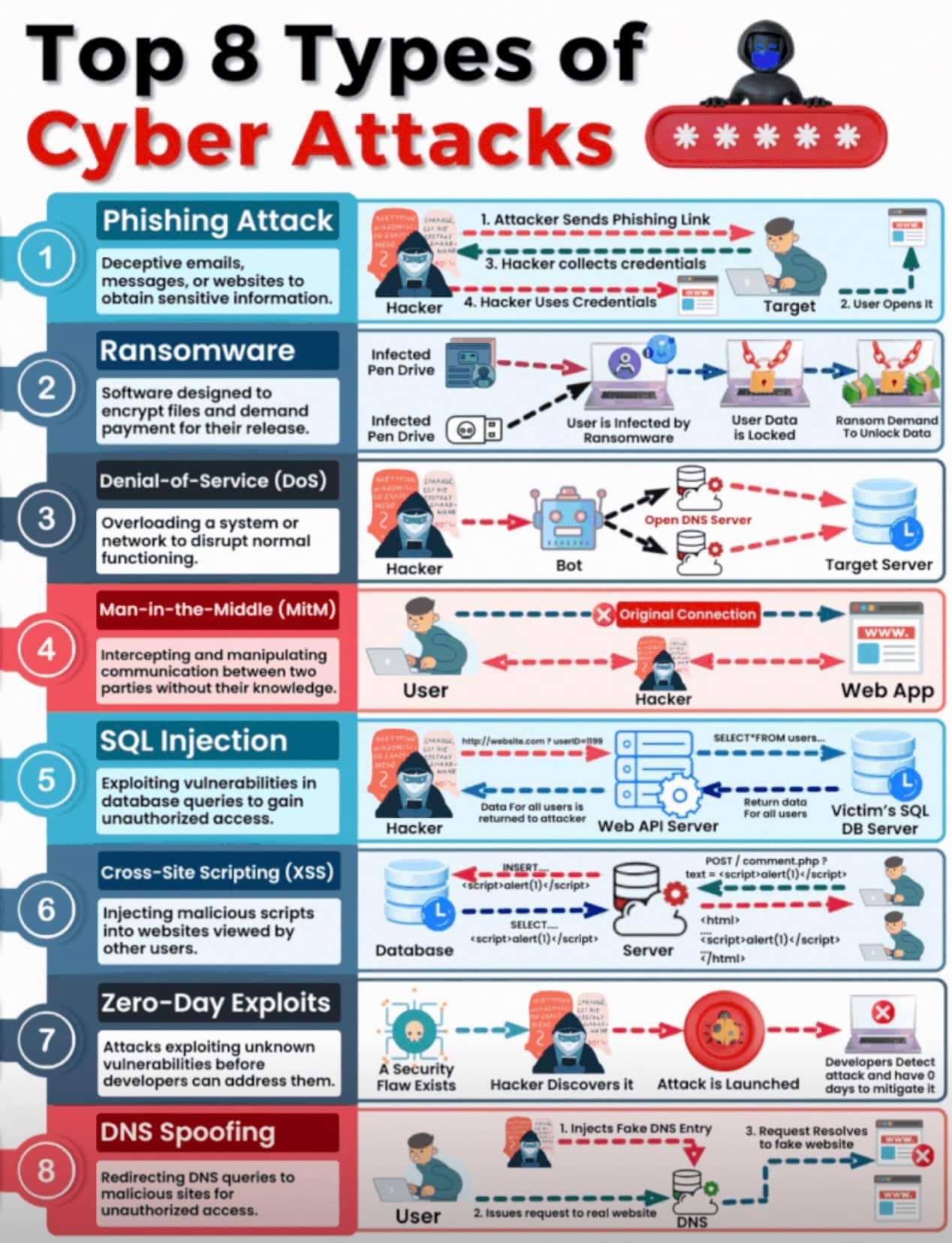
Understanding the Top 8 Types of Cyber Attacks
In today’s digital world, cyber threats are constantly evolving, targeting individuals, businesses, and even governments. Understanding different types of cyber attacks can help in developing effective defense mechanisms. Here are the top eight types of cyber attacks that pose serious risks to cybersecurity:
1. Phishing Attack
Phishing is one of the most common cyber threats. It involves attackers masquerading as trusted entities to trick users into revealing sensitive information, such as login credentials, financial data, or personal information. This is often done through deceptive emails, messages, or fraudulent websites.
2. Ransomware
Ransomware is a type of malware that encrypts a victim’s data, making it inaccessible until a ransom is paid. These attacks can cripple businesses and individuals alike, often demanding payment in cryptocurrency to evade tracking.
3. Denial-of-Service (DoS) Attack
A DoS attack aims to overwhelm a target’s server, network, or website with excessive traffic, making it unavailable to legitimate users. A more sophisticated version, Distributed Denial-of-Service (DDoS), involves multiple systems launching simultaneous attacks, making it harder to mitigate.
4. Man-in-the-Middle (MitM) Attack
This attack occurs when an attacker secretly intercepts communication between two parties. By doing so, they can steal sensitive information or alter communications. Common MitM techniques include Wi-Fi eavesdropping and session hijacking.
5. SQL Injection
SQL injection is a technique where attackers exploit vulnerabilities in databases by injecting malicious SQL commands. This can grant them unauthorized access to sensitive data, modify databases, or even delete critical records. Websites with poor security measures are especially vulnerable to this attack.
6. Cross-Site Scripting (XSS)
XSS attacks occur when an attacker injects malicious scripts into websites that are later executed by unsuspecting users. These scripts can steal user credentials, track activity, or spread malware. Websites that fail to sanitize user input are at higher risk.
7. Zero-Day Exploits
Zero-day attacks exploit undisclosed vulnerabilities in software or systems before developers have a chance to patch them. Because the attack targets unknown weaknesses, they are highly dangerous and difficult to prevent. Cybercriminals actively seek and trade zero-day vulnerabilities on the dark web.
8. DNS Spoofing
DNS spoofing, also known as DNS cache poisoning, involves altering DNS records to redirect users to fraudulent websites instead of legitimate ones. Victims may unknowingly enter sensitive information on these fake sites, leading to data breaches and financial loss.
Protecting Against Cyber Attacks
To defend against these cyber threats, organizations and individuals should adopt strong cybersecurity practices, including:
-
Using multi-factor authentication
-
Keeping software and systems updated
-
Avoiding clicking on suspicious links or attachments
-
Employing firewalls and intrusion detection systems
-
Regularly backing up important data
As cybercriminals continue to refine their tactics, staying informed and proactive is crucial in the fight against cyber threats. By understanding these attacks and implementing robust security measures, individuals and businesses can safeguard their digital assets.
-
-
Your blog post
My post content
-
Your blog post
My post content
-
Your blog post
My post content
-
Your blog post
My post content
-
Your blog post
My post content




